What is Hardening?
According to the National Institute of Standards and Technology (NIST), Hardening is defined as [1] “a process intended to eliminate a means of attack by patching vulnerabilities and turning off nonessential services”.
Hardening policies define security requirements to which all systems must meet. In some cases, these are defined and mandated by government regulations, but many businesses create their own security policies by adapting official benchmarks documents to their own business goals and security concerns.
The Figure 1 shows examples of the most common security standards which can be enforced depending on the business and specific country laws.

Security Benchmarks
To minimize the attack surface concerning default configurations, corporate hardening standards and guidelines need to be enforced. The Center of Internet Security (CIS) Benchmarks [2] or NIST’s guide to general server security [3] are good examples of broadly industry recognized documents that provide granular guidance to a company in the pursuit of safer systems.
The basic steps to apply a security benchmark are as follows:
- Determine the security configurations to which the infrastructure must comply with.
- Quickly identify the current state of the computer infrastructure against the benchmark’s requirements.
- Perform corrective actions where the system did not detect compliance.
CIS Benchmarks
One of the most relevant documents, when it comes to guidelines on security configurations, is the CIS Benchmark. This is a project maintained by the CIS [2] and “is the primary recognized industry-standard for secure configuration guidance, developing comprehensive, consensus-derived checklists to help identify and mitigate known security vulnerabilities across a wide range of platforms”.
This is an extensive document where each suggestion contains a detailed description of the issue it addresses as well as auditing, remediation steps and possible issues.
The Figure 2 is an example of configuration rules that exist on the benchmark for the Windows Server 2016.

Automation is key
From the get-go, the Benchmark documents are just that: documents in PDF format. These are typically long files, for example, the CIS Benchmark suggests 216 individual configuration guidelines for CentOS7 alone. In the case of a small company, this form factor may work, but for companies of considerable size with thousands of hosts it is unfeasible to manually check and remediate thousands of configurations.
Just like most processes when it comes to computer systems, automation is key and greatly reduces overhead. A study on tools that can verify benchmark’s configuration in an automated fashion must be a priority if one wishes to implement them.
The core aspect of these tools is that the documents are translated into code, which allows for automated evaluation of each rule. This enables security teams to further define processes to prevent attacks with minimal human error. Tools may also contain code for automated remediation, but one must keep in mind that this can break functionality of some machines and not all problems can be solved in this way.
A good payed option is the CIS SecureSuite® membership [4]. This is a service provided directly by the CIS, which is the maintainer of the benchmarks.
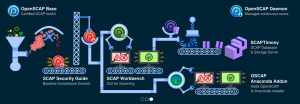
An open source way of automating configuration checks of not only the CIS Benchmarks but also several government mandated security policies, is the OpenScap project [5] which includes several tools for conformity enforcing. These tools use Security Content Automated Protocol (SCAP), a protocol maintained by NIST. Figure 3 illustrates how all the tools in this project work together.
Main issues and possible setbacks
There are a lot of variables to consider during a hardening process, especially when the concerning hosts have existed in a company for many years and configured in a time where security was not a priority. These are simultaneously the most vulnerable machines and the most difficult to implement hardening processes, especially if they are essential to business which they usually are.
A conformity project is a lengthy process that needs to be handled with care in order to provide the least impact to business. A configuration, although secure, may break the whole system and business applications. Because of this, there are always risks that must be accepted and changes that simply cannot be made, but that does not mean that these should be ignored. The risk should be identified, categorized, and monitored for possible exploitation. Risk assessment is of utmost importance and should be followed with a disaster recovery plan.
Conclusion
Security practices entail the identification of an organization’s information system assets and the development, documentation, and implementation of policies, standards, procedures, and guidelines that help to ensure the confidentiality, integrity, and availability of information system resources. When it comes to security standards, it is important to follow official guidelines, accepted by security professionals around the world as is the case of the CIS Benchmarks.
Maintaining a secure server requires constant effort, resources, and vigilance from an organization. It is important to keep in mind that the term “security compliance” denotes a process, rather than a state. A system is everchanging and security policies should change with it whenever needed.
The topic of enforcing security to old machines is not new, it is quite common for companies to have flawed systems that do their job well. These systems cannot be handled in an automated fashion as was previously suggested. Their context is important and manual revision is mandatory.
References
| [1] | National Institute of Standards and Technology, “Hardening,” U.S. Department of Commerce for Standards and Technology , 10 2015. [Online]. Available: https://csrc.nist.gov/glossary/term/Hardening. |
| [2] | Center of Internet Security , “Download Our Free Benchmark PDFs,” [Online]. Available: https://learn.cisecurity.org/benchmarks. |
| [3] | K. Scarfone , W. Jansen and M. Tracy , “Guide to General Server Security,” National Institute of Standards and Technology, 07 2008. [Online]. Available: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-123.pdf. |
| [4] | Center of Internet Security, “CIS SecureSuite® Membership,” [Online]. Available: https://www.cisecurity.org/cis-securesuite/. [Accessed 06 2020]. |
| [5] | OpenSCAP, “Security Compliance,” redhat, [Online]. Available: https://www.open-scap.org/features/security-compliance/. [Accessed 06 2020]. |
