Introduction
The need to overhaul La Redoute’s DNS platform stemmed from the appearance of limitations, risks that had become too restrictive in use and time-consuming processes. The necessity of automation, compatibility, and clear use of naming conventions had become too important.
In line with the ambitions defined for La Redoute, the architecture unit has endeavoured to follow certain requirements when building our DNS platform:
• Focus on turnaround time and scalability of the solution
• Offer services as a standards-compliant and robust platform
• Ensure availability, reliability and performance
• Provide a cost-effective self-service solution that offers APIs
• Leverage the benefits of the cloud
The opportunity presented by the decision to overhaul our private and public DNS infrastructures was an occasion to improve our security, our scalability and to take advantage of the benefits of cloud services. We were able to design a single foundation to automate the various actions of registering, renewing, updating domain names, etc.
You can find the previous article on our DNS platform which deals more specifically with the automation theme and a REX of the project: Our DNS platform: Back to the future
Reminder
DNS is the acronym for Domain Name System, which acts as a “directory” for the Internet. Its role is critical, particularly in establishing the correspondence between domain names and the IP addresses of servers. If a DNS cannot translate the domain name into a correct IP address, it will not be possible to access the website. In simple terms, without DNS, much of the internet as we know it collapses. For a company this means a total or partial loss of all its internet traffic on its front ends and other applications.
In this article we will discuss the path and challenges you will face in setting up your DNS platform.
It is important to understand the general functioning of DNS before reading this article, which will be mainly oriented on technical aspects and requires a certain mastery of the concepts.
DNS Resolution
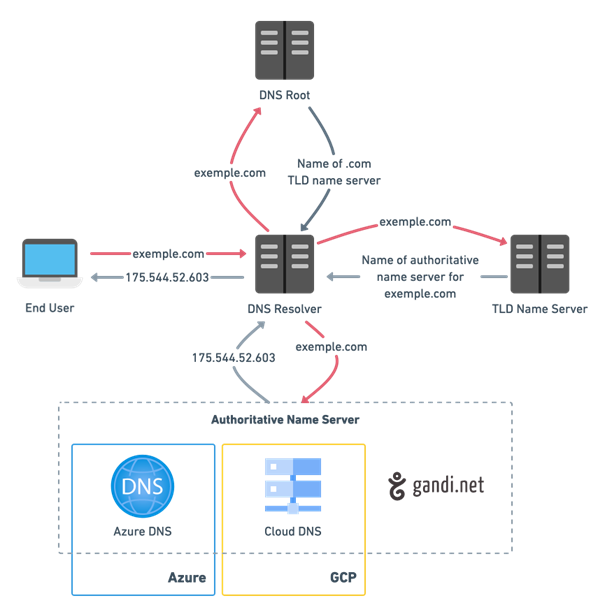
Let’s take the simple example of a resolution of a record type A
Record Type Value TTL
exemple.com A 175.544.52.603 10800
1. A user types example.com into a web browser and the request travels across the Internet and is received by a recursive DNS resolver
2. The resolver then queries a DNS root name server (.)
3. The root server then responds to the resolver with the address of a top-level domain (TLD) DNS server (such as .com or .net), which stores information for its domains. When we search for example.com, our query is directed to the .com TLD
4. The resolver then makes a request to the .com TLD
5. The TLD server then responds with the IPs of the name servers of the example.com domain. See the paragraph on NS records.
6. Finally, the recursive resolver sends a query to one of the authoritative servers for the example.com domain. This means that the authoritative name server hosts the mapping of the domain name to an IP address (which has been put there by the user). So there are no more redirects to other name servers, the authoritative name server returns the IP address of example.com directly (This is true in our example because it is an A-record, but in case of CNAME a new DNS resolution would be started).
7. The IP address of example.com is then returned to the resolver by the name server
8. The DNS resolver thenresponds to the web browser with the IP address of the originally requested domain
Split Horizon DNS
The split horizon DNS is a mechanism mainly used for security and privacy reasons.
An example of a use case is a server that has both a private IP address on an internal network (unreachable from most of the Internet) and a public address, i.e. an address that is reachable on the Internet in general.
Using split horizon DNS, the same name can lead to either the private or public IP address, depending on the environment of the client sending the request. This allows client machines on the internal network to access a server directly, without having to go through a router.
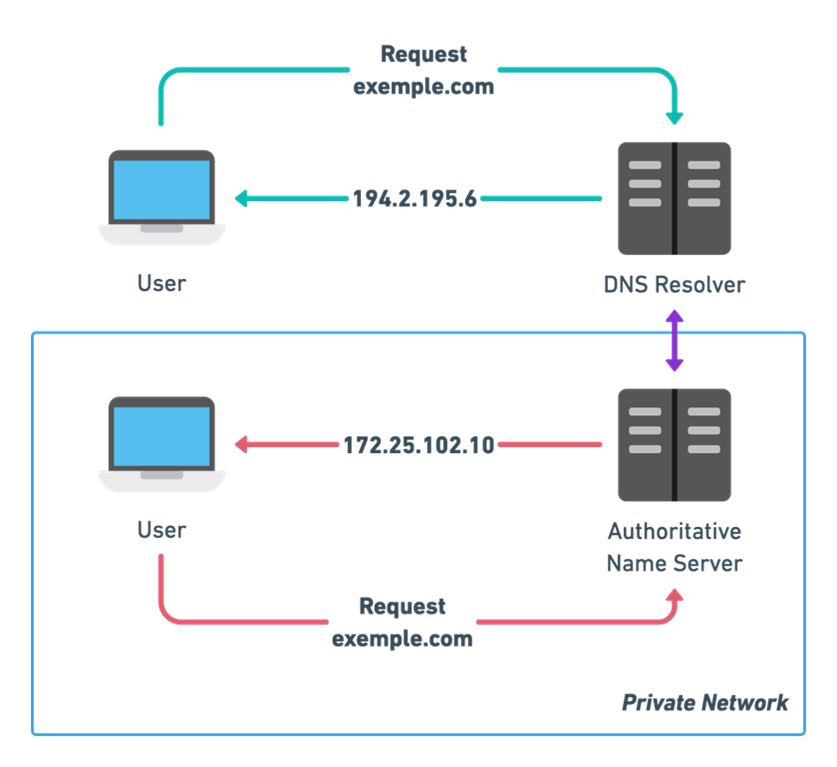
DNS queries for example.com received on the private IP address (172.25.102.10) receive a DNS response that contains an internal IP address; and DNS queries that are received on the public network interface receive a DNS response that contains the public IP address (194.2.195.6).
Automation
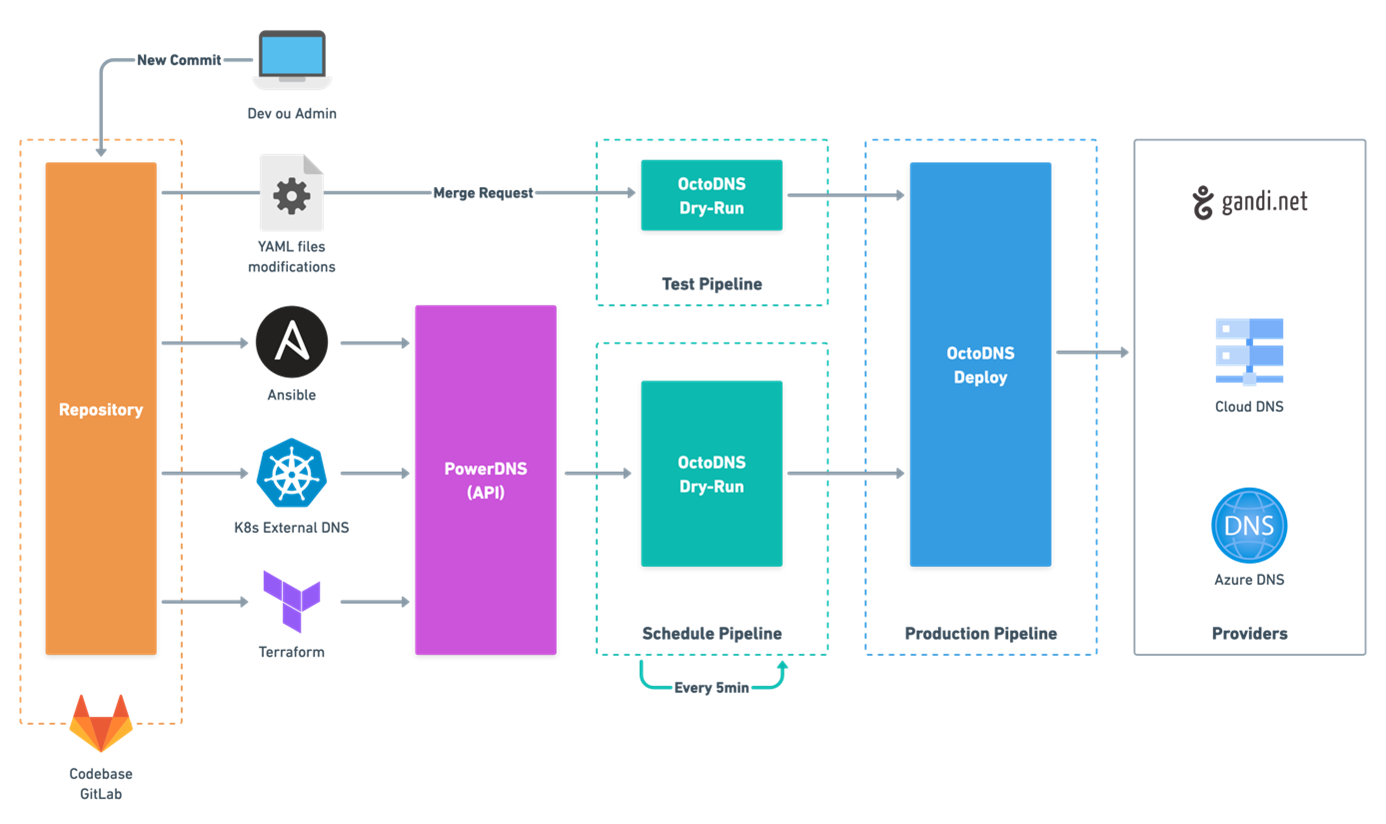
To find out why we decided to base our solution on PowerDNS and octoDNS I invite you to read the relevant sections in our previous article on the subject: Our DNS platform: Back to the future – laredoute.io
Several paths are available to manage our configurations on our various DNS providers:
• via PowerDNS for the IaC tools
• via a YAML file for manual modifications from the GitLab IDE
 Deployment pipeline diagram
Deployment pipeline diagram
Industrializing our processes with these tools has allowed us to capitalise on a single way of dealing with multiple DNS providers for both the private and public DNS platform. The result is a scalable product that allows us to be flexible and easily integrate new providers.
Registrar
A registrar has an administrative role concerning domain names and their associated services, in particular it manages the reservation of domain names. The registration of a domain does not automatically imply the provision of DNS services for the registered domain. However, in most cases, the registrar will also act as a DNS provider.
When you register a domain name, you must provide your registrar with accurate, reliable contact information and update it promptly if it changes during the registration period.
To register the domain name laredoute.fr, you must provide the registrar with the names of the DNS servers that will be the authority for the domain. The registrar sends this information to the registry of the TLD that has authority over .fr, and the latter adds an appropriate record.
 Generic diagram illustrating the registration process
Generic diagram illustrating the registration process
In this way, the TLD’s DNS servers will have the necessary information to return the addresses of the Authoritative Name Servers that correspond to the requested domain name when requested by a DNS resolver.
It is possible to run an authoritative name server yourself. However, in the majority of cases DNS Hosting services are used which are operated by companies such as: FreeDNS, Google Cloud DNS, Azure DNS, Gandi.net, GoDaddy, etc.
DNS Records
DNS records are sets of instructions found on DNS servers. These instructions are essential for a successful DNS lookup.
APEX Domain
A domain apex is the root of a domain. There is no subdomain part in a domain apex.
For example, https://laredoute.fr is a domain apex, because it is the “root” of the hierarchy of domain names. And https://www.laredoute.fr, aide.laredoute.fr, m.laredoute.fr are called subdomains of http://laredoute.fr.
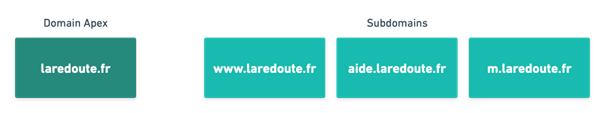
The difference between a domain apex and a subdomain is very important when working with website redirects or URL redirection. The zone apex is where the SOA and NS records for a DNS zone are placed.
Subdomains should employ a “CNAME record”, while domain apex redirects typically require the use of a “A record”. Although not expressly forbidden, many DNS service providers do not allow the creation of CNAME records for zone apex records.
If you want to go more deeply in the detail of why you can’t have a CNAME at the zone apex, I advise you to read this article of the Internet Systems Consortium (ISC): CNAME at the apex of a zone
Specificity of ALIAS/ANAME Record
As explained in the above paragraph you cannot put a CNAME record at the zone apex, that’s why some DNS providers have offered custom solutions that allow CNAME-like behaviour on the zone apex. They are more likely to be name ALIAS record or ANAME record.
A Record
Associates a domain name with an IPv4 address. This type of DNS record is used to connect the domain or subdomain names of your website, such as redoute.com , to a numeric IPv4 address.
Most of the applications that scale with automatic procedures will have their IP adresses that change over time, that’s why it’s recommended to rather use the DNS name of the service to reach the target.
Record Type Value TTL
redoute.com A 217.70.184.55 10800
CNAME Record
Is used to specify that a domain name is an alias for another domain name.
Record Type Value TTL
www.redoute.com CNAME webredir.gandi.net. 10800
A CNAME record doesn’t require a hard-coded IP address, as we’ve gone through above, and allows your infrastructure provider to manage any IPs related or associated to your domain. The limitation being that CNAME records usually can not be used to configure the root domain, and are therefore not available at the apex domain.
NS Record
Is used to specify which name servers are responsible for managing the DNS records for the domain.
NS records, known as “name server” records, a domain often has several NS records that can indicate the primary and secondary name servers for that domain.
Record Type Value TTL
laredoute.com NS ns-221-c.gandi.net. 10800
laredoute.com NS ns-232-a.gandi.net. 10800
laredoute.com NS ns-38-b.gandi.net. 10800
MX Record
Associates a domain name with an email server, and also specifies a weight used for prioritising the resolution of the request.
These records allow the SMTP protocol to determine to which server an e-mail should be routed.
Record Type Priority Target TTL
redoute.com MX 0 redoute.com.mail.protection.outlook.com. 3600
Securing your records
You will have understood that a domain name is a very important corporate asset and that the strategic decisions that revolve around it must be relevant to best protect the interests of its brands.
From domain name registration to business intelligence on the deployment of new generic top-level domain names (gTLDs), each stage of the registration life cycle must not be neglected.
Cyber-attackers are already taking advantage of a wide range of possible attacks on DNS servers such as DNS spoofing, DNS tunneling or DNS hijacking, so don’t leave them any good opportunities on your domain names either.
WHOIS
WHOIS is the system that asks the question: “Who is responsible for a domain name or IP address? Many registrar services offer a public WHOIS lookup tool, for example: Whois: Domain name search on Gandi.net
ICANN is committed to maintaining unrestricted public access to accurate and complete WHOIS information. To this end, registrars and registries provide public access to data on registered domain names.
Example of a data extract available following a WHOIS query on laredoute.fr:
type: ORGANIZATION
contact: LA REDOUTE SAS
address: LA REDOUTE SAS
address: 110 rue de blanchemaille
address: 59100 ROUBAIX
country: FR
e-mail: 137c9a830504c142965ea2db8783e915-35138037@contact.gandi.net
registrar: GANDI
WHOIS protection
To prevent personal information from being publicly accessible, it is advisable to use this type of service, which not only allows you to hide your sensitive data, but also guarantees protection against the threat of spam, by preventing your e-mail address from being listed.
Registry Lock
The registry lock is a security mechanism used to protect domain names from possible attacks. It is generally set up by the organisations responsible for managing TLDs (e.g. Afnic for .fr).
It allows the owner of a domain name to indicate to the registry that he or she wishes to lock the information in the domain name, thus preventing all operations and updates that could be carried out without the owner’s knowledge. This lock can be lifted permanently or temporarily by means of a double authentication and verification process specific to the Registry Lock used.
The use of a registry lock is one of the recommendations listed by the ANSSI in its good practice guide: Publication: Best practices for the acquisition and use of domain names
TMCH – Trademark Clearinghouse
A database of validated and registered trademarks established by ICANN to help trademark holders prevent illegal behaviour in the DNS.
Trademark holders have the opportunity to register their trademarked domains first when a new generic extension is opened for registration.
DPML – Domains Protected Marks List
A mechanism for defending the reputation of one’s brand online and thus protecting one’s business from possible attacks before they occur. To take advantage of the DPML program, trademarks must be registered in the TMCH database. DPML protection disappears once the trademark registration expires.
A mechanism that proactively blocks the registration of all domain names that partially or totally include the name of the brand. This provides a truly preventive brand protection strategy that defends the company’s online reputation and protects it from possible attacks before they occur.
Adultblock
Protects its trademarks from cybersquatting by restricting registration for all adult domain name extensions for ten years, including the TLDs: .xxx, .sex, .adult and .porn.
Email security
With the widespread use of digital technology, customers and companies are at the forefront of spammers and phishers. Their objective is clear: to hack into users’ accounts and collect as much information as possible (passwords, bank accounts, credit cards, etc.). Phishing is one of the most used attack vectors for many reasons, including the fact that e-mail is easy to spoof. A well-known brand logo alone can instantly legitimise an email in the eyes of many users.
Companies are therefore putting strategies in place to protect themselves and their customers as much as possible.
 High level treatment scheme
High level treatment scheme
SPF Record
The Sender Policy Framework (SPF) record is entered as a TXT record. The entry contains a list of IP addresses from which mail from this domain can be sent.
SPF records are one of the mechanisms that rely on DNS to help mail servers confirm whether a mail is coming from a trusted source. With this type of record, it is more difficult to impersonate a domain, which reduces the likelihood of attacks.
• Example of a SPF lookup on laredoute.fr
v=spf1 include:spf1.laredoute.fr include:spf2.laredoute.fr include:spf3.laredoute.fr include:spf.protection.outlook.com include:spf.mailjet.com include:spf.prosodie.net ~all
The include mechanism makes it possible to allow 3rd-party IP addresses defined in another SPF record to be included in the “master” SPF record.
• Result of a lookup on spf1.laredoute.fr
v=spf1 mx include:spf-00168301.pphosted.com +all
• Result of a lookup on spf-00168301.pphosted.com
v= v=spf1 ip4:XX.XXX.XXX.XX ip4:XXX.XXX.XXX.XX
DKIM – DomainKeys Identified Mail
DKIM is an email authentication method that prevents spammers and other malicious third parties from impersonating a legitimate domain. It collaborates with SPF and DMARC to safeguard email transmission. Messages that fail the DKIM check might then be rejected or filtered out by the receiving mail server.
DKIM signatures are based on the use of two keys:
• A public key is published in the DNS records, and receiving servers can use the key to decode the signature
• A private key is store secretly and used to generate a hash of the message
When an email is sent, the hash of the message generated with the private key is encrypted using the public key. Then the message is sent along with the encrypted hash. When the message is received, the recipient uses its private key to decrypt the hash and verify that it matches the original content of the message. Any agent in the message’s transit path has the ability to validate the message signature.
• Example of a DKIM lookup on laredoute.fr with a specific selector
dkim:newr.onmicrosoft.com.:selector1-laredoute-fr
v=DKIM1; k=rsa; p=Public Key;
For more informations on DKIM check the RFC 6376: RFC 6376: DomainKeys Identified Mail (DKIM) Signatures
DMARC – Domain-based Message Authentication Reporting and Conformance
DMARC is a proposed standard that allows senders and receivers of e-mail to co-operate by sharing information about the e-mail they send to each other. Senders’ communications can be authenticated with these details, which help to improve the mail authentication architecture. It also gives legitimate domain owners the ability to request that fraudulent messages be immediately classified as spam or rejected altogether.
DMARC tells the receiving mail server what to do after checking the SPF and DKIM records of a domain.
• Example of a DMARC lookup on laredoute.fr
v=DMARC1; p=none; pct=100; rua=mailto:reports@redoute.com
Final Word
In conclusion, the domain name system plays a crucial role in the security and functioning of the internet. With the increasing reliance on the internet for communication and access to information, it is essential to ensure the security of DNS. This includes protecting DNS servers from attacks and ensuring that DNS data is accurate and up to date. Additionally, the continued development and implementation of new technologies, such as DNSSEC, can help to further improve the security of the DNS. It is important to set up and use these technologies in order to safeguard your online communications. By working closely with the registrar, individuals and organizations can ensure that their DNS and mail protection strategy is properly implemented and effective in protecting their online assets.