The importance of gathering information
To start a pentest it’s important to collect information about the target in the first place, this also includes to define the goals and the objectives of the test. The information gathering consists in the search for public information available related to the system and seeks what are the best way to exploit that information.
The purpose of gathering as much information as we can, is to understand how the application or system works in order to discover security lacks that can be solved. For that process we have two approaches:
Passive Information Gathering – this method can be used before the active information gathering, because is less evasive. Only the publicly published information of the target information is used, and it is gathering as much information as possible without establishing contact between the pentester and the target. For this we can use some open source tools, for example: whois domain, social networks, mail servers, list of applications hosted on the same IP address and other open information.
Active Information Gathering – on this type of approach, more preparation is required from the pentester because it leaves traces, which can result in the trigger of alerts to the target. Using this method, the targeted organization may become aware of the ongoing process since there is an active engaging with the target. At this stage, we obtain information about the open ports, services, versions of the applications, version of the operating system, etc.
Toolset of the pentester for scanning
Now that we know what information we want to retrieve, there’s many ways to gather it. The very first tool that everyone should use is Google. The amount of data shown by Google is huge and you can find interesting things regarding your target. The Google Hack Database shows you a big list of useful tricks to look for information with the Google Search Engine. Maltego is also another tool that help link data with business and email addresses. Looking for information in that way is called indirect but it’s not enough to retrieve all that we want.
It was mentioned in the previous article that the main tool of a pentester is a security-oriented operating system. There’s three major one: Kali, ParrotSec and BlackArch. They provide all the tools needed to quickly run a penetration test against an environment. Among all of them, there’s some that are mainly used for scanning and information gathering:
- nmap – is an open-source network scanner used to discover hosts and services on a computer network by sending packets and analyzing the responses, it can also be used to vulnerability scan.
- OWASP ZAP – is an open-source web application security scanner. It is intended to be used by both those new to application security as well as professional penetration testers.
- nslookup – this is an available command-line tool in every computer for querying the Domain Name System to obtain domain names or IP addresses or even other DNS records.
Many other tools exist but are more specific depending on the results of the ones mentioned above. For example, if you find a database server listening on a port that can be contacted via a client software, you could use it to try and connect to the service. This led to further research afterward and the deeper you go, the better the result.
Scan the host and network with Nmap
To perform a discovery on the network of the target, we can use the Nmap tool. It helps identify hosts and services on a network. On this case if we want to scan a host, we can obtain information about the ports that are open, the services that are running, the version of the operating system, etc.
There are many commands we can do in Nmap, but we’ll show you two case:
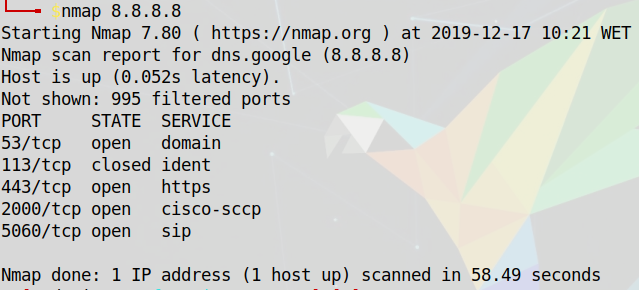
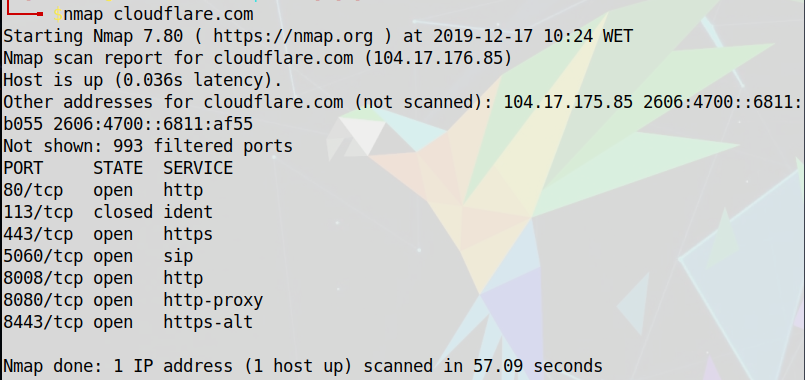
In these two images we can see examples of the output that the Nmap retrieves. We can see the open and closed ports, the services that are running behind the ports and if the network have other addresses.
Scan the website with OWASP ZAP
OWASP, which stands for Open Web Application Security Project, is an online community that produces numerous resources in the field of web application security. More than the famous OWASP Top Ten project, they provide a tool called ZAP, Zed Attack Proxy. It helps find security vulnerabilities within a web application with the help of tools like Scanner, Spider, Fuzzer, etc.
After launching ZAP, the software shows you a quick start window where you can put the target URL and perform a quick scan and vulnerability analysis on the web application. This is the easy first step with the software.

You can also setup ZAP as a proxy for your browser, so every request that is made will go through ZAP and will be analyzed.
However, the most efficient method is to manually use each tool provided to you:
- With the Spider, you’ll be able to crawl through a website. The software will try to retrieve every link and page that it could find within the scope you specified.
- With the Fuzzer, if you want to perform a big number of requests by changing one or more parameter each time, it will help you defined rules about it
- With the Active Scanner, you will perform various attack and it will show you how vulnerable is the application
ZAP have many more feature in it, and yet it’s one of the most powerful software for web vulnerability scanning.
What is interesting ?
We can collect a lot of information about the target, and now it’s important to filter what is useful for the pentest. By default, everything needs to be kept and no information is useless, but some are more interesting for a pentester. For example: services running on the host, software versions, name and email of the company employees, IP addresses, hostname and architecture. Everything that could be an entry point for an attacker is a critical information.
Now that we have enough information about the target, the pentester can draw a threat map of the network or the application. He focuses on the vector he considers easy to use and start the exploitation according to that. In the next part of this series, we’ll talk about the exploitation and how we can use what we find during the scanning phase. Andreia Francisco from Security team was also a contributor for this article.
