Identify interesting information
There are many types of vulnerabilities ranging from simple disclosure of information to remote code execution, and it could be either harmful or critical for the information system. For example, vulnerabilities that let an attacker steal sensitive data or disrupt a lot of servers are considered the most dangerous ones. Also, a good way to identify interesting vulnerabilities, is to analyze if it could be exploitable.
The most valuable flaws that should be investigated are:
- Cross Site Scripting (XSS) which can be stored or reflected in the URL parameters. It lets the attacker execute a script in the browser of a user. It is often used to steal sessions and cookies.
- Remote Code Execution (RCE) lets the attacker run code on a machine with a specific user. For example, a web server using Apache has a user with same name running the process and is often used to execute commands on the host if it is not hardened enough.
- SQL Injection (SQLI) related to databases. It is a vulnerability where the attacker can use an unprotected user field to perform a direct query to the database. Often seen on login forms.
- Cross Site Request Forgery (XSRF/CSRF) is a kind of attack where the malicious command is transmitted by a user trusted by the application. In the end, the user is performing actions he is not aware of.
Gain access to the target and elevate your privileges
Now it is a matter of exploiting the most severe and dangerous holes of the target and finishing with the analysis of the less critical ones. The easiest vulnerabilities are exploited first in the context of a penetration test where time is the key.
When a vulnerability is potentially exploitable, there are several resources available to quickly get your hands on an exploit. Websites such as Exploit-DB contain a huge database of known vulnerabilities and some have an associated and proven exploits.
Tools such as Metasploit has many scripts using known exploits readily available.
There are three steps to a successful vulnerability exploit:
1. Get the right target and its vulnerability
2. Set up the payload
3. Gather information about the exploitation of this vulnerability
Depending on the vulnerability and the payload, you may not have the full admin account on the host or the targeted application. Another step is to gain more access or to escalate privileges. This can be performed via multiple ways and is related to the target configuration and environment.
If you manage to use an SQL Injection, you may want to target the database where the account and password are stored. If you used a vulnerability to gain access on a host, you could find an executable with high privileges and use it to your advantage.
Classify vulnerabilities to quickly determine the critical ones
To facilitate not only the mission of the pentester, but also the priorities of security managers, it is important to understand the impact of all the vulnerabilities found and order them by severity.
To classify a vulnerability, you need to think about 3 points:
- How easy it is to exploit it?
- How dangerous it is?
- How much effort is needed to fix it?
Each point gives a different amount of severity level. For example:
- A vulnerability which is difficult to use and is not dangerous to the target will not be critical at all.
- A vulnerability which is easy to exploit, but harmful to the target could be a low priority for the security team.
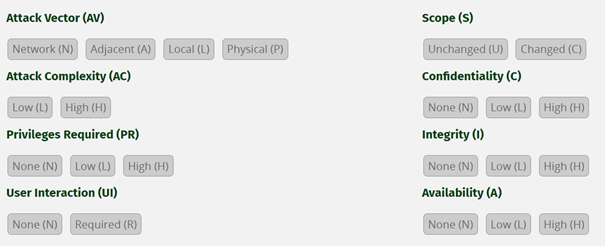
Figure 2 contains the list of all criteria that are part of the Common Vulnerability Scoring System (CVSS). Each point defines the characteristic of the vulnerability.
Here is a glimpse of the different values that helps to score the vulnerability accordingly:
Attack Vector: It specifies how close the attacker needs to be to the target to use the vulnerability. “Network” is the furthest and “Physical” is the closest.
Attack Complexity: Determine the amount of effort and rate of success if the attacker manages to exploit the vulnerability. A high complexity means the attacker needs a huge amount of preparation and time. It also means that the vulnerability is related to conditions beyond the attacker’s control.
Privileges Required: If the attacker needs permissions on the target to perform the exploit then the vulnerability will be less critical.
User Interaction: If the attackers must have a user to interact with him, it means that this kind of vulnerability will be harder to use.
A calculator is available (https://www.first.org/cvss/calculator/3.1) to perform the scoring. A vulnerability can a have severity between 0.0 and 9.0.
Writing the report and conclude the pentest
The last part of a professional pentest is writing the report. This document contains all the discovered and exploitable vulnerabilities of the target. It allows the client to classify and prioritize the problems and add the effort factor for each one.
To conclude, pentesting is a technical discipline but also requires a lot of resourcefulness and imagination. The best pentesters have a great deal of technical knowledge but are also people who believe that any information could be exploitable. This article is the last one of the “Pentest” Series which includes an Introduction and an article focusing on Information Gathering and Scanning.
